Connect
Categories
- EU NIS 2
- 3 LoD
- 3lod
- Accounting Standards
- AI
- Audit
- Automotive Security
- blockchain
- Capital
- CISA
- ciso
- Cloud
- Cloud Security
- cloudsecurity
- CMMC
- CNI
- coap
- Compliance
- CRA
- Credit Rating
- Credit Ratings
- Credit Risk
- Credit Risk Management
- criticalnationalinfrastructure
- Crypto
- Crypto Exchange
- Crypto Regulation
- Cryptocurrencies
- CSF Profiles
- CUI
- Cyber
- Cyber Attack
- Cyber Audit
- Cyber Compliance
- Cyber Crime
- Cyber Incident Reporting
- Cyber Insurance
- Cyber Law
- Cyber legal
- Cyber Reglation
- Cyber Regulation
- Cyber Regulation (Apologies-nowwithpost)
- Cyber Regulations
- Cyber Regulaton
- Cyber Resilience
- Cyber Resilience Act
- Cyber Resilienceact
- Cyber Risk
- Cyber Risk Framework
- Cyber Risk Management
- Cyber Risk Management Framework
- Cyber Security Risk Management
- Cyber Strategy
- Cyber Supply Chain Riskmanagement
- cyberattack
- cyberattacks
- Cyberawareness
- Cyberawarenessmonth
- Cyberchange
- cybercomplexity
- cyberDefence
- Cybereducation
- cyberegulation
- Cyberessentials
- CyberGovernance
- Cyberharmonisation
- Cyberincident
- Cyberins
- Cyberpolicy
- cyberreglation
- cyberrisk
- cyberriskframework
- Cybersecurity
- Cybersecurityframeworkprofiles
- Cyrpto Regulation
- dataprotection
- Defence
- Defence Industry
- Defence Industrybase
- Defenceindustry
- Defense
- Defense Industry
- Defense Industrybase
- Defense IP
- departmentofjustice
- DFARS
- DHS
- DIB
- Directors and Officers
- Directors and Officersinsurance
- disinformation
- DoD
- DORA
- DoT
- DSEI2023
- economicgrowth
- Encryption
- ENISA
- EU
- EU Cyber Law
- EU NIS 1
- EU NIS 2
- eudora
- EUrope
- EV
- EV Cyber
- EV Security
- evcyber
- EVinfrastructure
- False Claims Act
- falseclaimsact
- fbi
- Federal Reserve
- federalreserve
- fiduciaryduty
- Financial Control
- Financial Institutions
- Financial Markets
- Financial Services
- Financial Services Industry
- financialaudit
- financialoversight
- financialservices
- financialstability
- FISMA
- Fitch Ratings
- fraud
- fraudprevention
- geolpolitics
- Geopolitical Cyber
- Geopolitics
- Geopolitics Cyber
- Governance
- Governance.
- Howgate Sable
- incidentresponse
- infrastrcturesecurity
- Insurance
- Insuranceindustry
- insurancelitigation
- intelectualproperty
- Intellectual Property
- Internal Audit
- IoT
- IoT Security
- IP
- IP Theft
- iptheft
- ITAR
- japan
- Left of Bang
- leftofbang
- Legal Risk
- legalrisk
- Liquidity
- lloydsoflondon
- Manufacturing Cyber
- manufacturingcyber
- meDIBank
- merck
- MoD
- National Security
- NATO
- ncs
- NIS 2
- nis2
- NIST SP 800 171
- NSA
- nydfs
- ofac
- ONCD
- Operations Technology
- Organisational Design
- otsecurity
- pakistan
- PCAOB
- privateequity
- processautomation
- propertyandcasualtyinsurance
- ransomeware
- Ransomware
- Regulation
- Regulatory Capital
- Regulatory Compliance
- Regulatory Oversight
- Regulatory Risk
- regulatorycapital
- regulatorycompliance
- regulatoryreporting
- Reinsurance
- Resilience
- risk
- risktransfer
- rmf
- Sarbanes Oxley
- sarbaneSarbanes Oxleyley
- SDLA
- SDLC
- Securities and Exchange Commission
- Shared Resonsibility Model
- Shared Responsibility Model
- sharedresonsibilitymodel
- shareresponsbilityDefenseel
- Small Business
- Small Business Cyber
- smallbusinesscyber
- sme
- Solarwinds
- solvencyII
- Supply Chain Risk
- Supply Chain Risk Management
- Supply Chain Security
- supplychainsecurity
- The Augusta Group
- The Securities and Exchange Commission
- theaugusagroup
- theaugustgroup
- toyota
- uber
- Venture Capital
- Whistleblower
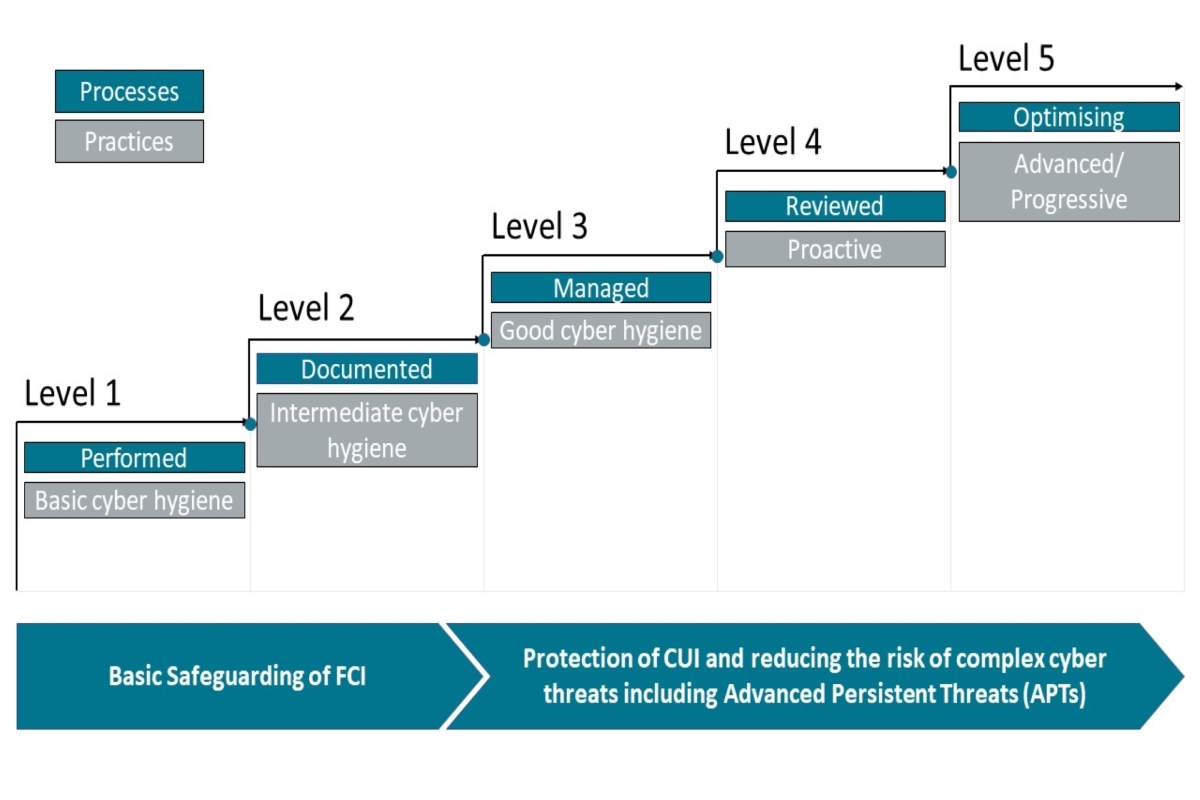
 CMMC is being driven forward by the US DoD as the standard for Cyber Security oversight and assurance across it’s Defence Industry Base (DIB). With between 300,000 and 350,000 companies in the supply chain, ranging from SMEs up to large corporates will be impacted by the programme. 5 levels of maturity certification have been defined based upon a companies holding of FCI or CUI data. With companies processing FCI data will have to comply with up to 72 cybersecurity practices. Those processing CUI will be assessed as a level 3 and above, required to comply with up to 171 cybersecurity practices as defined by NIST 800 171 r2.
CMMC is being driven forward by the US DoD as the standard for Cyber Security oversight and assurance across it’s Defence Industry Base (DIB). With between 300,000 and 350,000 companies in the supply chain, ranging from SMEs up to large corporates will be impacted by the programme. 5 levels of maturity certification have been defined based upon a companies holding of FCI or CUI data. With companies processing FCI data will have to comply with up to 72 cybersecurity practices. Those processing CUI will be assessed as a level 3 and above, required to comply with up to 171 cybersecurity practices as defined by NIST 800 171 r2.